Private companies and public services have a common goal: ensuring the security and accuracy of large amounts of data. To achieve the security needed in a large-scale context, the Federal Police, for example, implemented ABIS technology to bring together data from across the country into a national biometric database.
Most sectors are moving toward the digital world, which causes an increase in data production and the fragility of this information as well. The security mechanism present in ABIS for identifying people is biometrics, used by police authorities and by other sectors of the economy.
This technology already has a high rate of adherence and effectiveness. According to Experian's Global Fraud and Identity Report 2022, 93% of Brazilians consider the technology as the most secure for a digital experience.
To understand more about how the ABIS system works and is used, continue with me!
What is ABIS?
ABIS stands for Automated Biometric Identification System. The system's main objective is to identify individuals. To do this, it uses biometric characteristics, unique to each individual, in large biometric databases in a fast, accurate and scalable way.
In general, ABIS is used by law enforcement agencies to automate the verification and identification of individuals and to correlate people to events by collecting fingerprints from crime scenes. It is also used to identify duplicates in bank records and large e-commerce sites to prevent fraud and scams.
Now that we know what ABIS stands for, let's see how it works.
How does ABIS work?
Generally ABIS can be used to verify several types of biometric characteristics, primarily facial and fingerprint recognition.
In this explanation we will focus only on fingerprints.
The ABIS verification process starts by collecting the biometrics that will be used in the process. This collection can be done at biometric collection points for official documents or directly from crime scenes through forensics. It is also possible to capture fingerprints through the camera of cell phones.

The result of the collection is a biometric template. More about it below.
What are biometric templates?
Biometric templates are captures of an individual's physical characteristics converted into a format that can be easily compared and archived in computers. The most common types of biometric templates are:
- Fingerprints.
- Face shape.
- Irises.

In the case of fingerprints, the palms of the hands, feet, and fingertips have a series of lines that can end or bifurcate into well-known patterns.
These patterns are known as minutiae. It is by comparing the minutiae that similarities between two or more models are checked. See below:

The identification and extraction of these patterns along with the subsequent recording in a digital format that is easy to compare, archive, and manipulate are essential to the operation of a good biometric system.
This process is commonly called Enrollment. Learn about the steps:
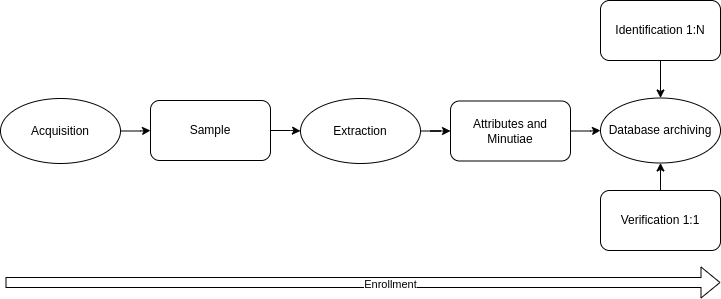
The first part is the acquisition of a biometric sample. After this, ABIS must extract the minutiae, also called attributes.
Right after that the template can be saved in the database and processed for identification or verification. More about this will be said shortly.
There are several formats available for storing biometric templates in a database. The best known is WSQ (Wavelet Scalar Quantization) created by the FBI and NIST.
There is one point of greater importance that deserves more attention: the format of the biometric template should combine as much information as possible without affecting the ability to compare two different templates and storage issues.
Verifying Biometric Templates
After extracting and storing the biometric template, it is time to process it. This is when ABIS shows its value.
There are basically two ways of processing in ABIS: verification and identification.
In verification, ABIS compares two biometric templates using an algorithm that specializes in finding the degree of similarities between these templates. In a criminal ABIS, at the end of the process, a parole officer can attest to the veracity of the process, which greatly speeds up his or her work.
This process is known as 1-to-1, ehich means this process takes place from one processed model compared to another unique model. Verification must be an extremely fast process, almost instantaneous, and we will see why in a moment.
Now learn how to practice verification and identification of biometric templates.
Identifying biometric templates
The identification process, also known as 1-to-N or 1-to-many, is the similarity checking of a biometric template against a large number of other templates.
The number of templates varies depending on how you use ABIS. You can handle thousands or even hundreds of millions of templates.
To make this possible, ABIS needs the biometric template verification process to be extremely optimized and accurate. Therefore, ABIS uses certified proprietary algorithms that meet the requirements of regulatory and standardization bodies. The best known certifications of biometric verification algorithms are MINEX III, FRVT, and iBeta Spoofing and Liveness.
Once the identification is complete, ABIS will create a list of templates that have achieved a minimum similarity score. With this list in hand, an operator can certify the outcome of the process, automate decision making, or generate reports.
What does the ABIS infrastructure look like?
Running a large-scale ABIS is not a simple task.
It is about operating a system that can deliver sufficient performance to execute thousands of transactions per second. For this, a demand-responsive infrastructure is required. A number of clustering, load distribution, and high-performance computing techniques are required to run an ABIS.
In addition, you need servers with large amounts of RAM and CPU to optimize the process. Every millisecond counts when it comes to processing thousands of biometric templates in the shortest possible time.
For legal and security reasons, the entire environment must be tested and always have the latest updates available, since extremely important data is at stake.
ABIS as a service
As mentioned earlier, the infrastructure required to run an ABIS is complex to manage. However, you can avoid this kind of problem by using ABIS delivered as a service.
In this mode, the ABIS infrastructure is managed by a specialized company that offers ABIS as a service that can be purchased and then paid for on a usage basis. Using ABIS in the cloud can accelerate its use for many different types of services.
Still, an application does not always need all the processing power of a large-scale ABIS.
There are cases where just a few isolated functions, such as biometric template verification, proof of life, or image enhancement and quality control, can revolutionize a conventional web application.
More security and accuracy with ABIS technology
ABIS is a rapidly growing technology, given the urgent demand for systems with biometric capabilities.
Whether it is to provide more security for your customers or to meet the needs of public agencies, the usability of the system can help both civil society and the state due to technology and innovation.
Managing an ABIS locally can be a challenging task. However, with the help of options such as ABIS as a service or biometrics APIs and SDKs solutions, any current web application can enter the world of biometrics and develop in the biometric application market.

